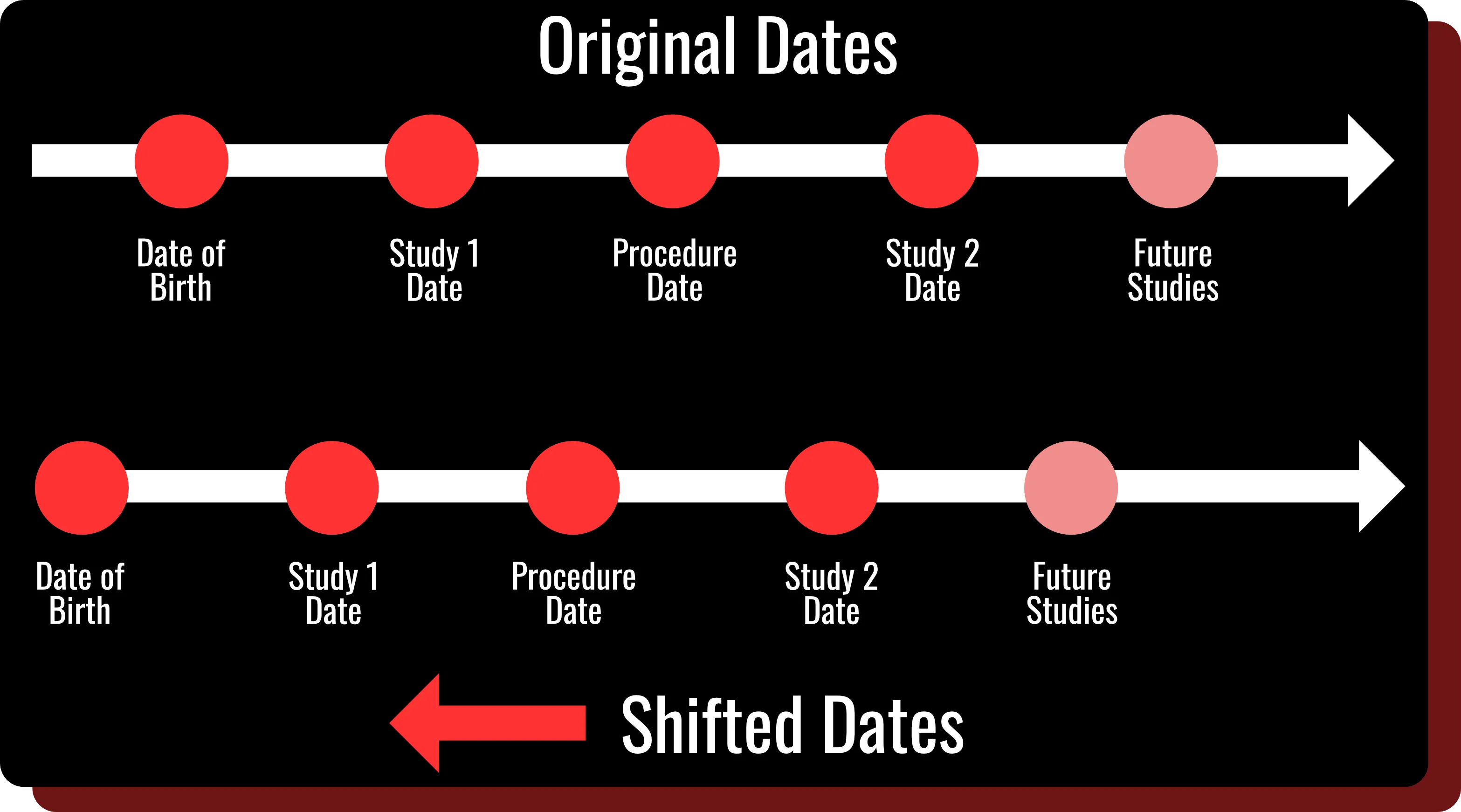
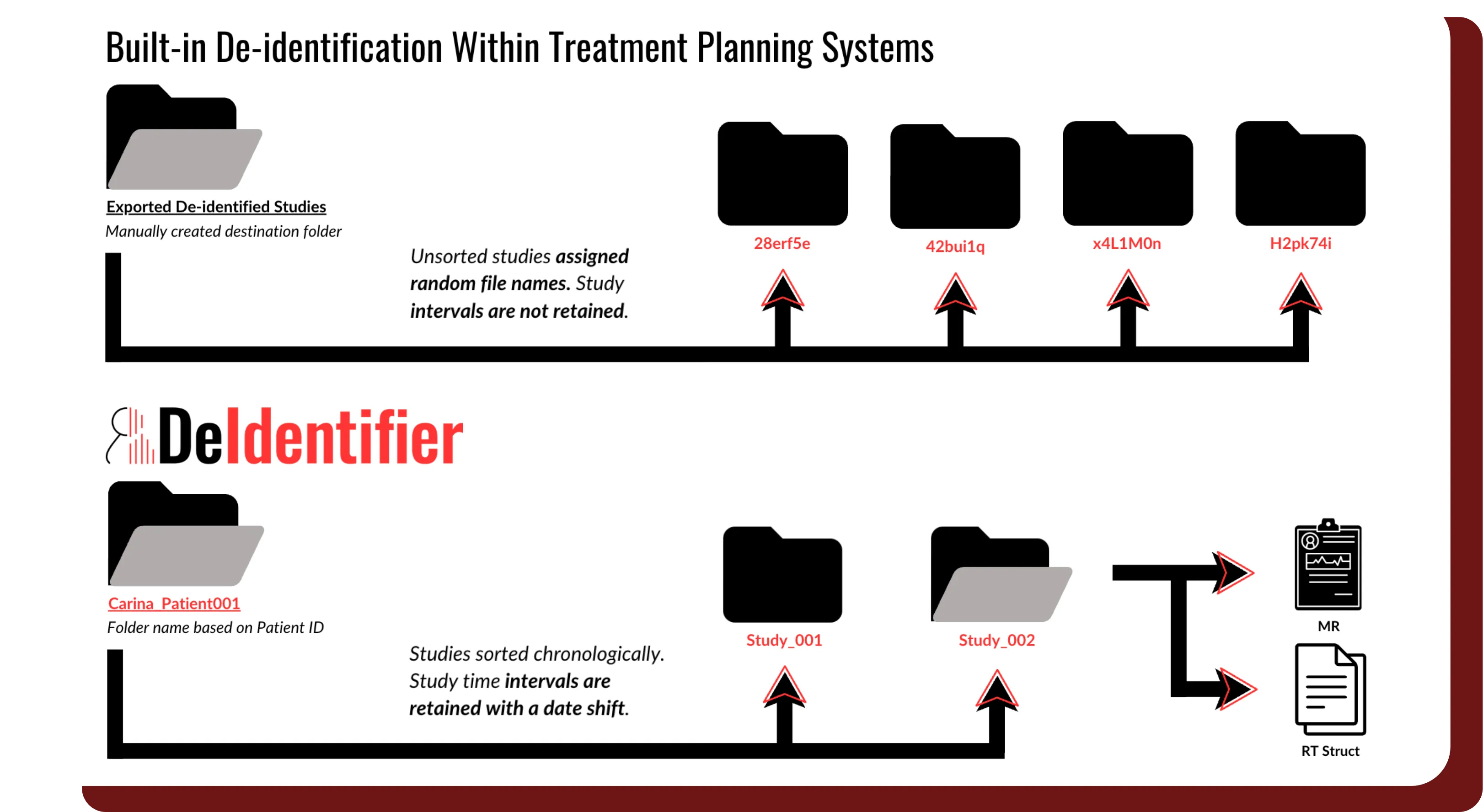
Study Interval Retention
- Automatically shift all dates within DICOM headers and clinical data using a patient-specific random number.
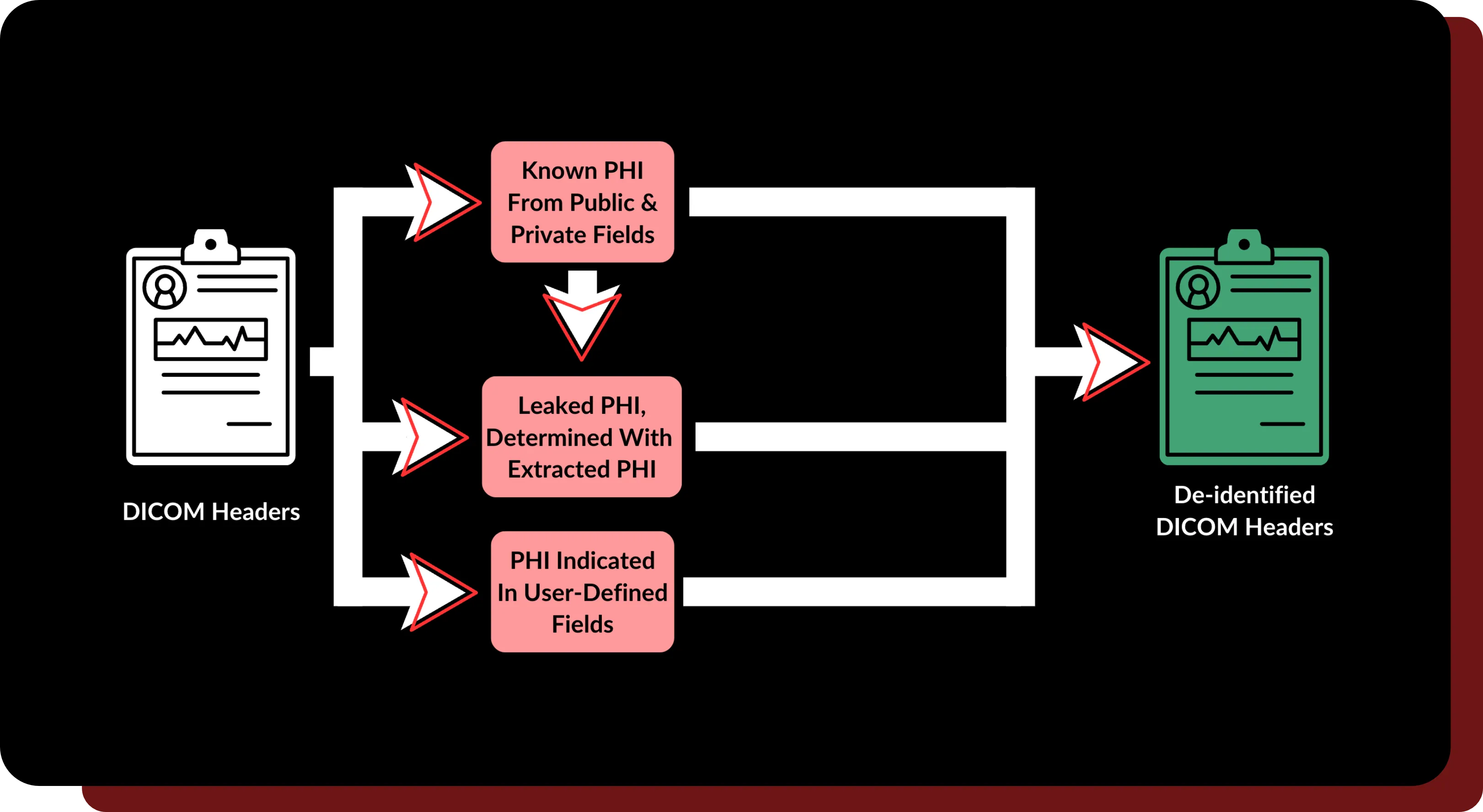
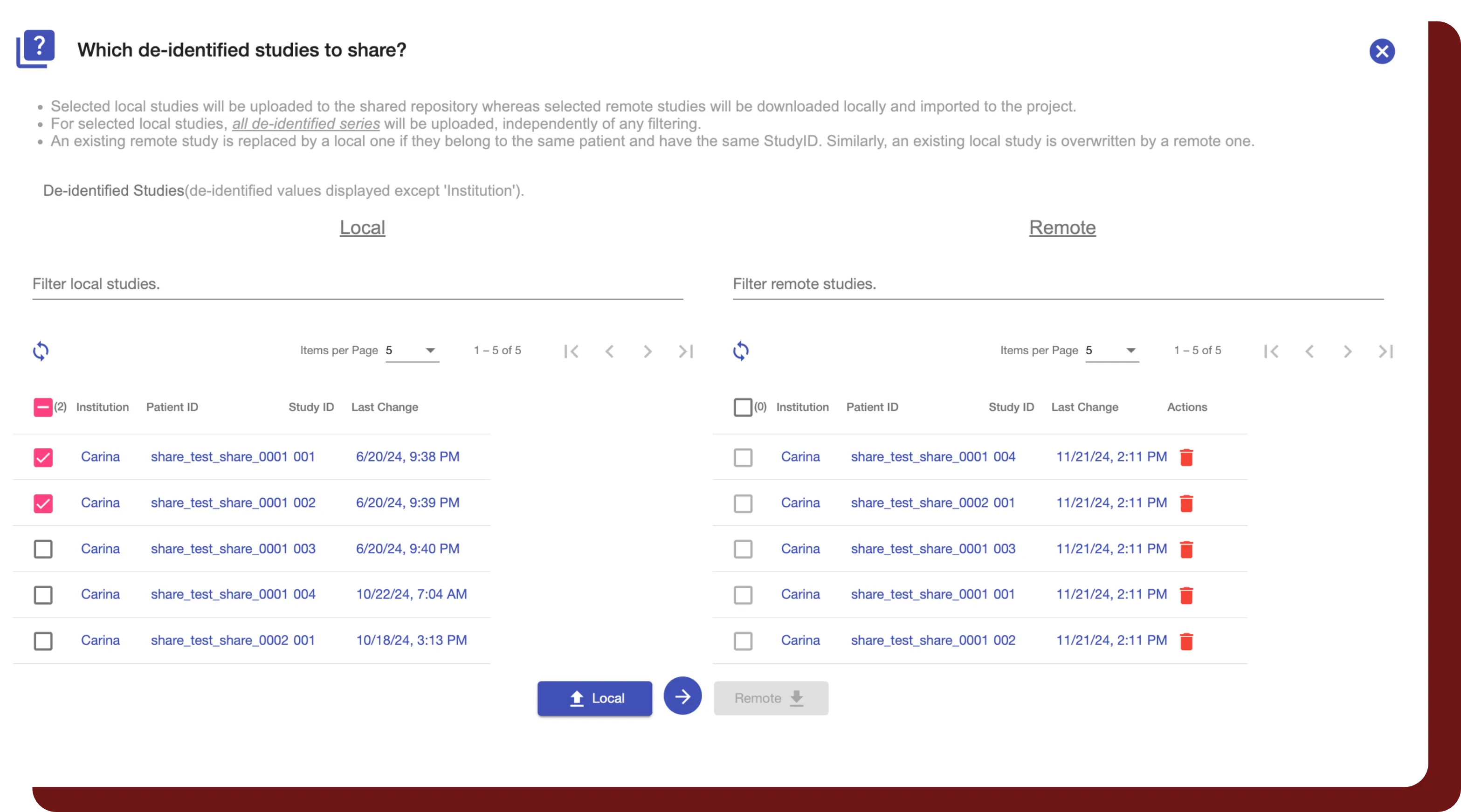
Redundancy Checks
- Multi-stage secure checks during de-identification prevent unexpected PHI leaks from all DICOM headers.
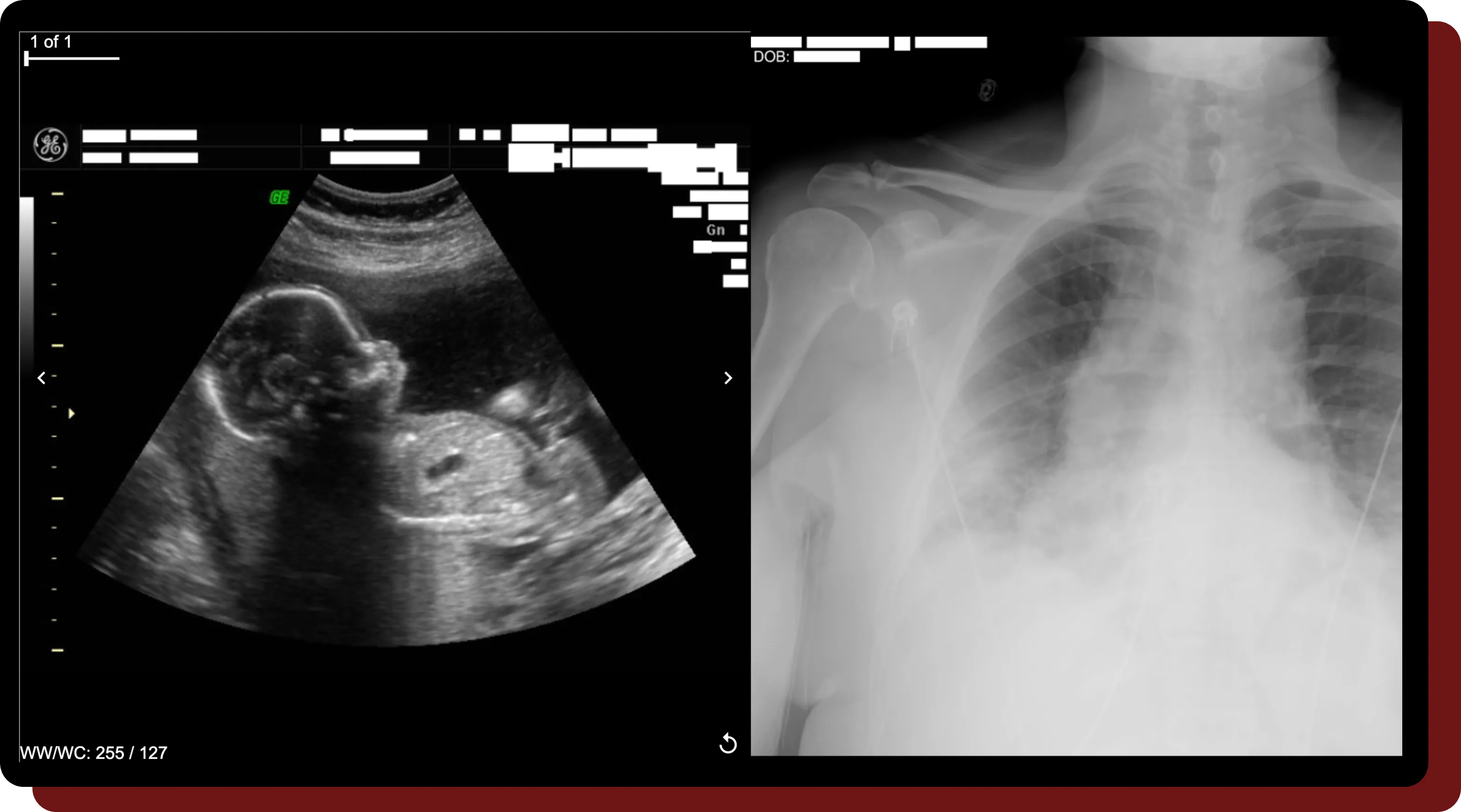
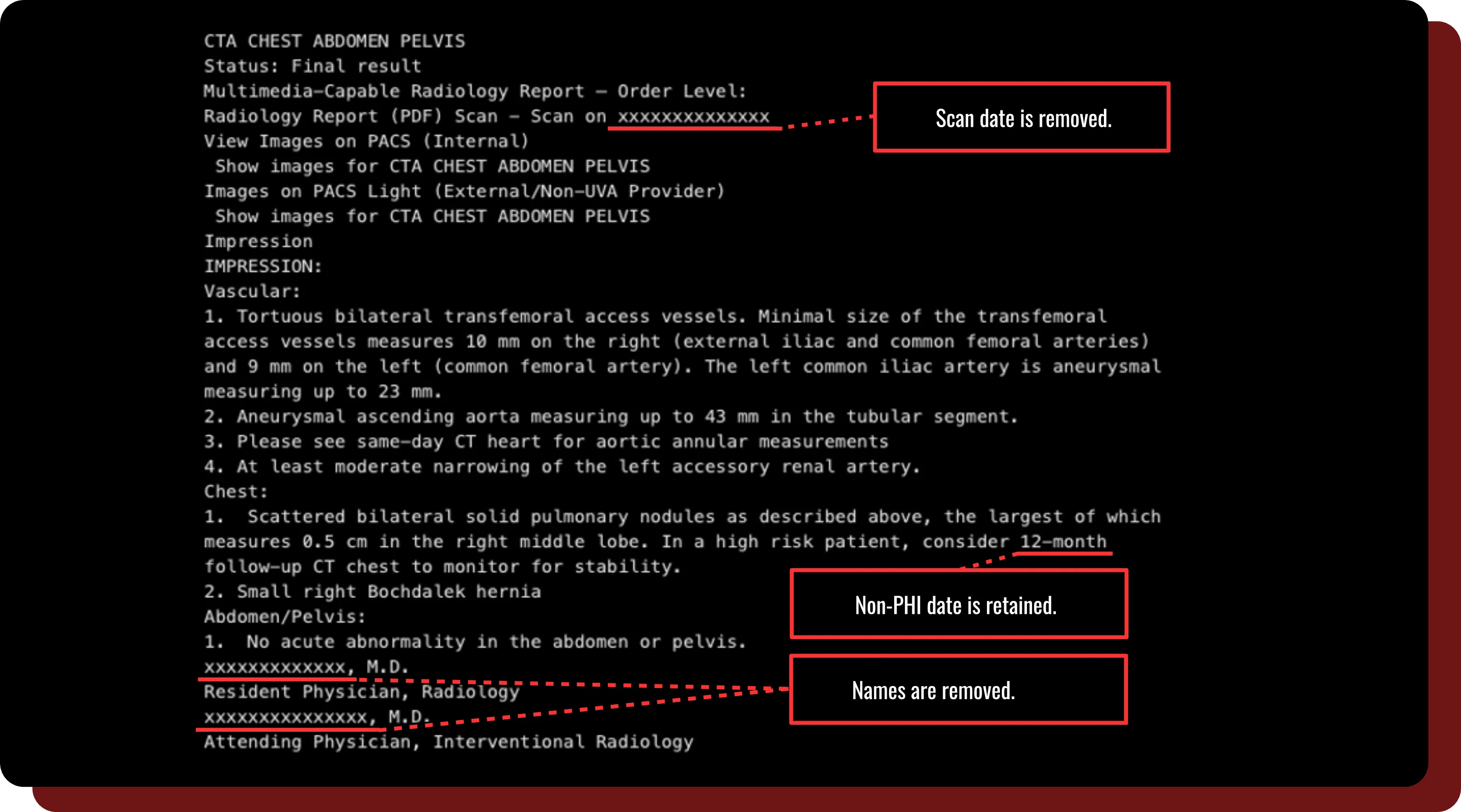
Burned-in Text Removal
- Text detection via natural language processing removes PHI text & retains key information, such as orientations.
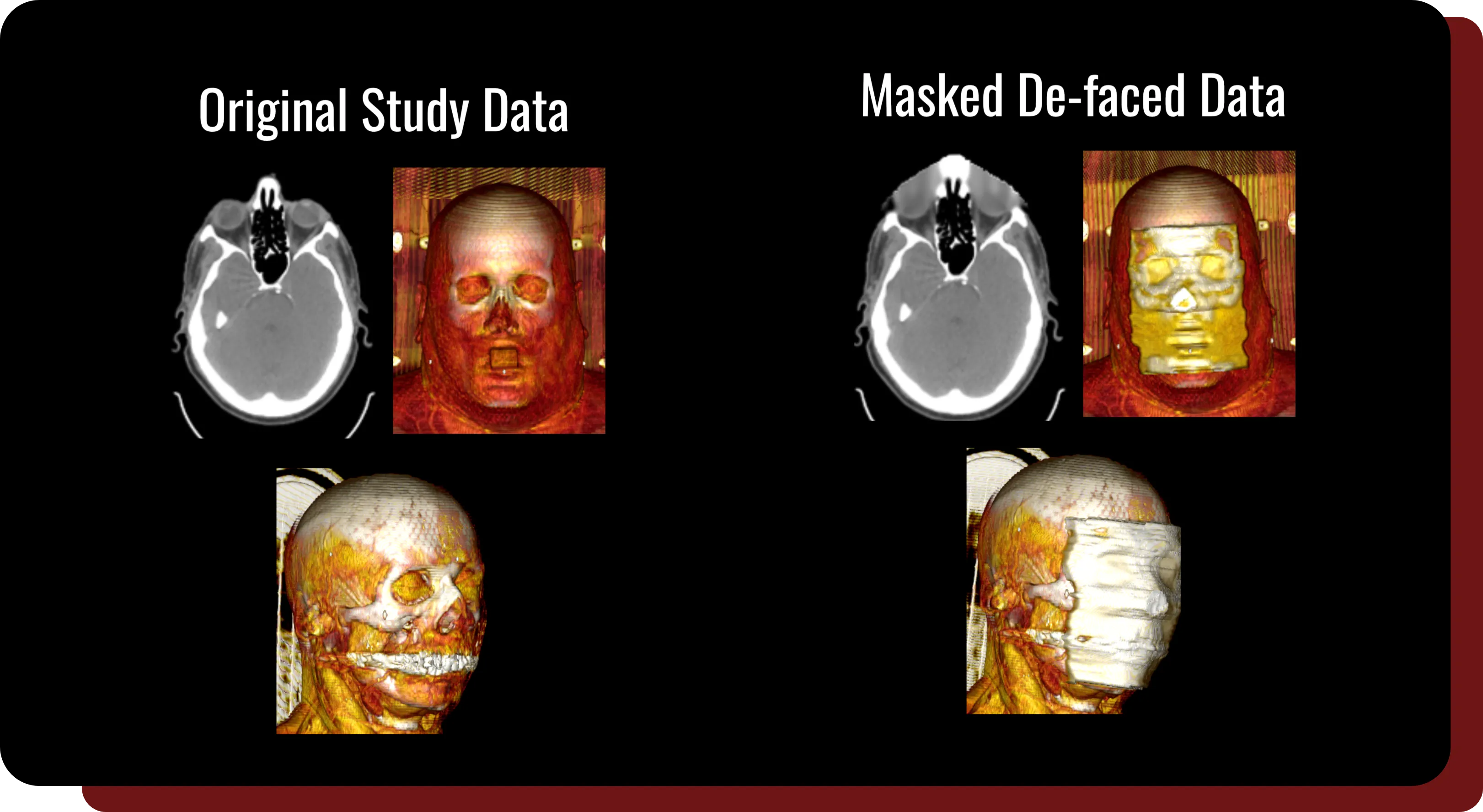
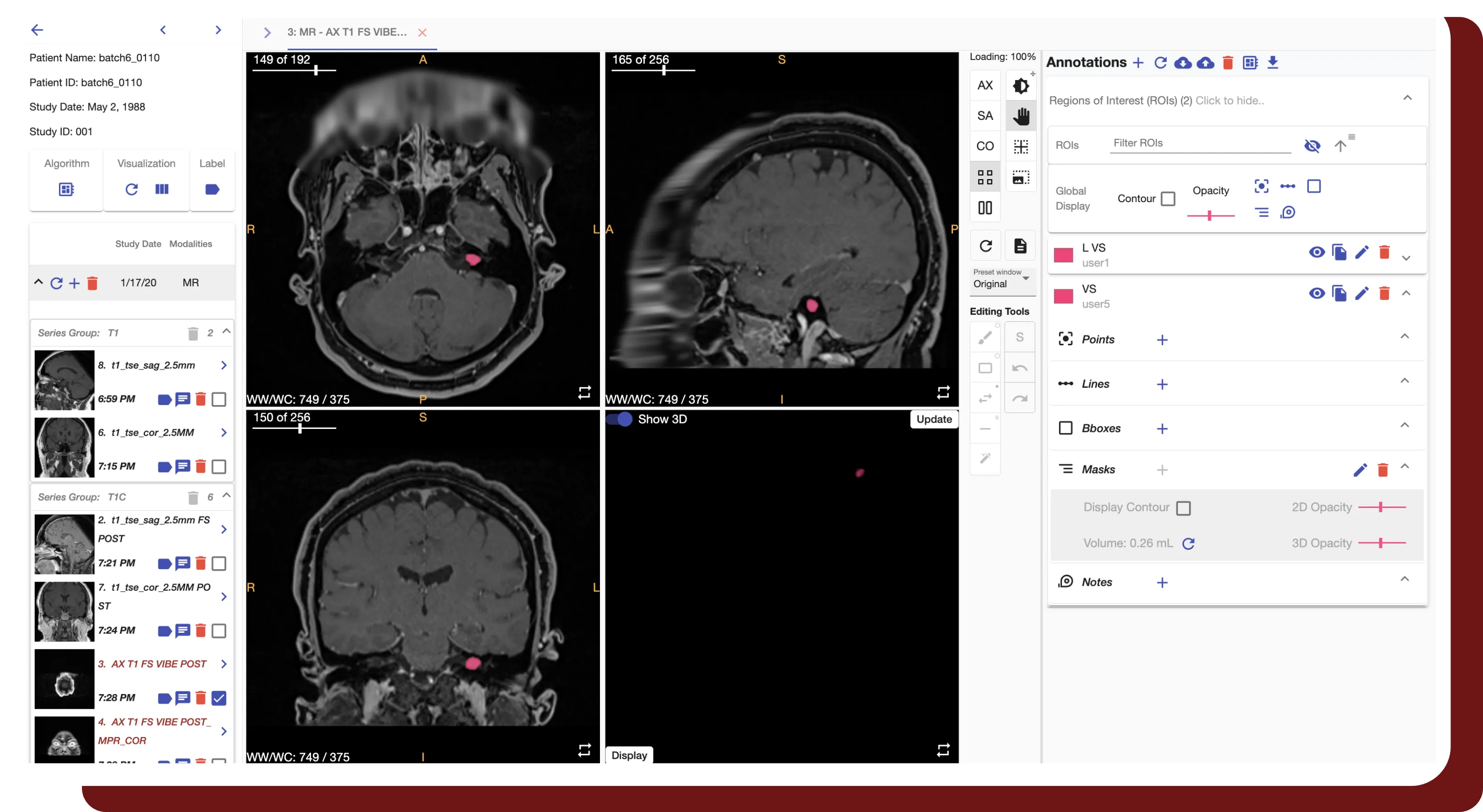
Masked-Based Defacing
- Our patented defacing algorithm generates a smooth mask to eliminate facial features with minimal image distortion, with negligible differences demonstrated for radiomics calculations and AI model training for internal structures*.
- Our algorithm provides robust support for CT and MR, with extended compatibility for PET-CT, RT Image, RT Dose, and RT Structure Sets by applying the same mask.
- Allows for fused multi-modality inputs with registration.
* Organs that are touching the mask, such as the eyes and nose, will be affected.
Report De-identification
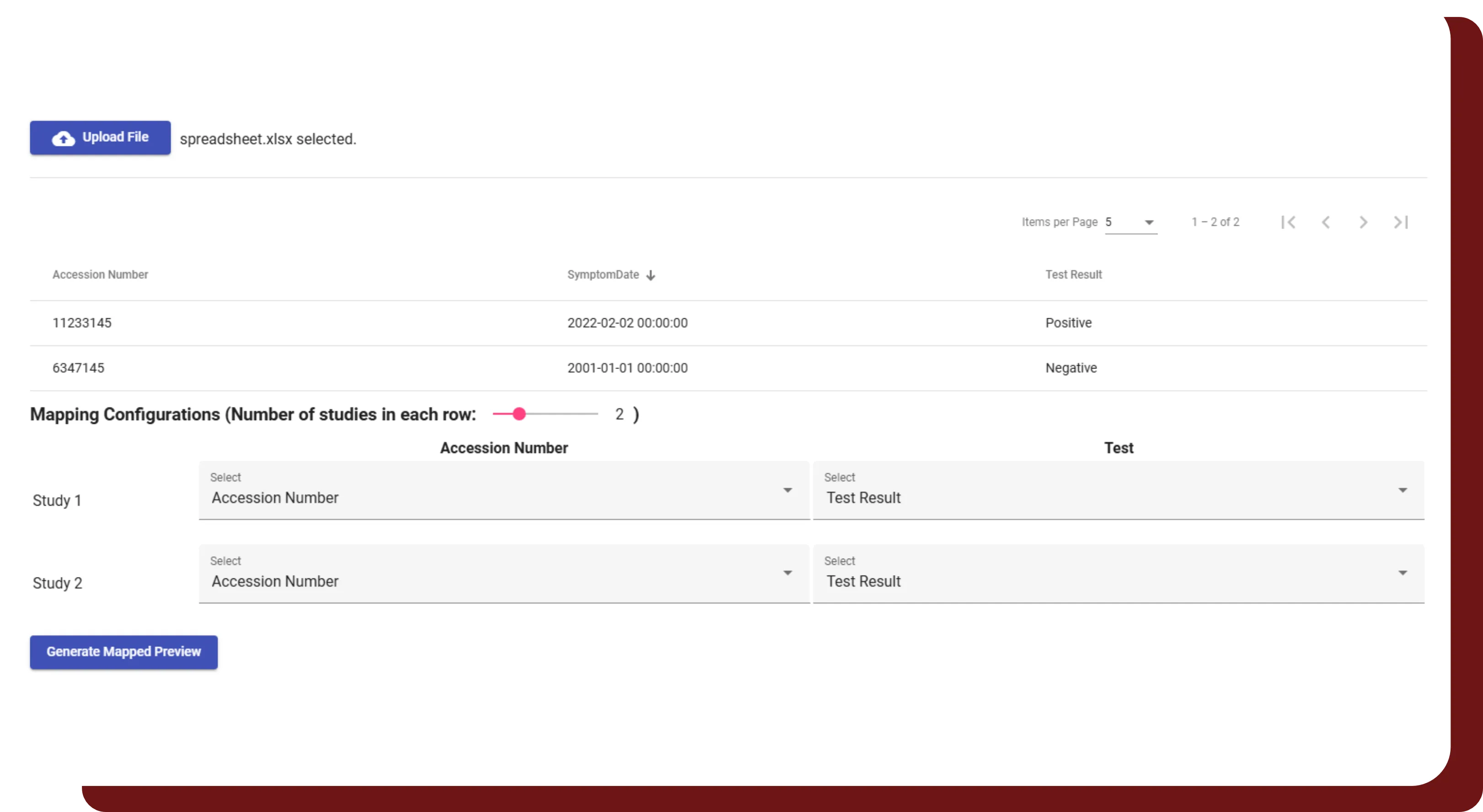
- Text-based reports can be uploaded, added to a project, and automatically de-identified to remove PHI using DeIdentifier’s state-of-the-art large language model.